Delivering industry-specific risk assessment, recommending policies and procedures, network security, and cloud security architecture with smooth implementation, monitoring, and maintenance to prevent emerging threats proactively.

How it works
A few simple steps to simplify your Cyber and Information Security challenges.
-
01 Get in touch with our security advisor
-
02 Choose your security Solutions
-
03 Let us do the heavy lifting
-
04 Enjoy our single pane of glass visibility
Why choose us
User friendly interface,
very easy to use
Most of our solutions are the Gartner magic quadrant leader in its domain. We master the hacks of putting the right solutions with the right set of configurations. This leads to increasing security posture and you achieve the best compliances, eventually easing the burden of your security insurances. To learn more follows us and engage with our consultants.


Streamline your Cyber Operation , Achieve the compliinace
Our Cyber and Information Security services are aimed at providing you with the right solution. Which Eventually streamlines your cyber operations. This will ensure your Information Security and help mitigate risk. We help you achieve the compliance; that your Industry demands.
Cyber and Information Security Services
Our certified team of experts help you bring the most pressing security need the industry is facing now a days
Vulnerability Management
Essential for identifying, assessing, and mitigating security vulnerabilities
Governance Risk & Compliance
Compliance automation monitoring, analyzing risk patterns, and enhancing decision-making to streamline processes for efficient governance.
CSPM : Cybersecurity Posture Management
Our continuous detection & remediation of misconfigurations improves your CSPM, as we build across your hybrid clouds.
CSIRT Cyber Security Incident Response Team
Our Computer Security Incident Response Team (CSIRT) is a group of IT professionals dedicated to managing and responding to cybersecurity incidents.
Awareness Training
We specializing in most Industry leading Cyber Awareness system and deliver integrated one stop solutions to businesses.
Secure Service Edge
We specialize in implementing various Secure Service Edge, and Cloud Access Security Brokers (CASB) to enforce security policies for cloud applications. Also, our Zero Trust Network Access (ZTNA) ensures that access is granted based on strict identity verification and least-privilege principles.
DLP: Data Loss Prevention
Our DLP solutions ensure your entire spectrum of diverse enterprise Infrastructure and rigorously protect and detect in real time.
Email Security
Our Email security ensure wide range of TRAP , TAPS and Ai powered tools to ensure secure message flows .
Watch latest Cyber news
Seamlessly Manage IT, OT & BYOD Environment
Our Expert vulnerability management helps you streamline your scanning reporting and remediating. We manage your External Attack surface management and internal comprehensive detection simultaneously. Allowing your Security team precision-driven priority remediation.
Our OT team safeguards your ICS, SCADA and PLC Infrastructure. We leverage industry-specific compliance frameworks to help you strengthen your security posture.









“With Canadians and Canadian businesses living and working online more than ever, cyber security has never been more important. While large scale cyber incidents can seem overwhelming, individuals have the power to strengthen our country’s overall cyber resilience. I encourage Canadians of all ages to participate in Cyber Security Awareness Month and learn simple and proactive measures they can take to defend against cyber threats.
– The Honourable Bill Blair, Minister of National Defence
DR Evolution of Acronis
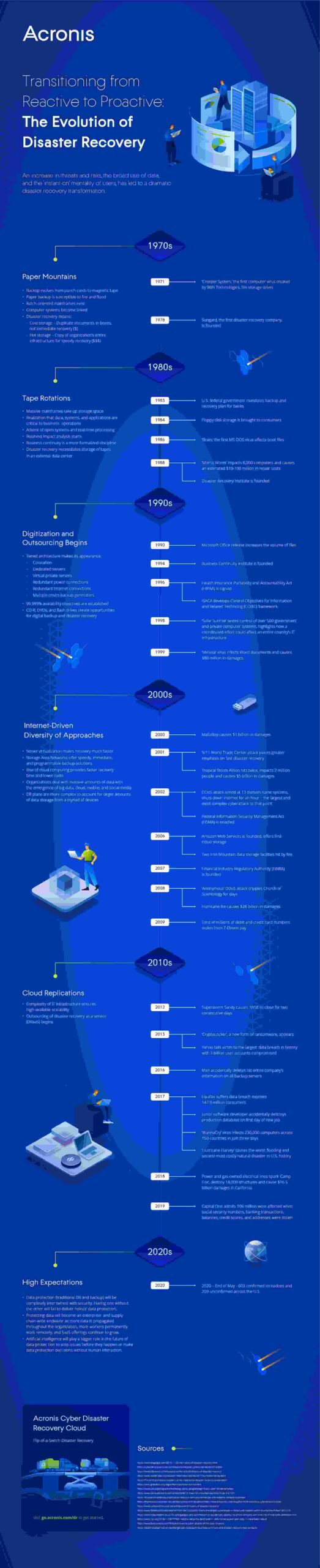
Assessing your organization’s cybersecurity maturity using the NIST Cybersecurity Framework (CSF) involves evaluating how well your current practices align with the framework’s core functions: Identify, Protect, Detect, Respond, and Recover.
Here’s a step-by-step guide to help you get started:
- Conduct a Self-Assessment
- Review the Framework Core
- Map Current Practices
- Identify Gaps
- Use Maturity Models
- C2M2 (Cybersecurity Capability Maturity Model
- NIST CSF Tiers
- Develop a Maturity Assessment Tool
- Questionnaires and Surveys
- Scoring System
- Perform a Gap Analysis
- Analyze Results
- Prioritize Gaps
- Develop an Improvement Plan
- Set Goals
- Action Plans
- Continuous Monitoring and Improvement
- Regular Reviews
- Adapt and Evolve
By definition, Operational Technology (OT) security refers to the practices and technologies designed to protect the systems that manage industrial operations and critical infrastructure.
Our OT security assurance includes:
- Integrity: Ensuring that the data and commands within OT systems are accurate and have not been tampered with.
- Safety: Protecting the physical safety of people and equipment by preventing unauthorized access or malicious actions.
- Availability: Ensuring that OT systems are available and operational when needed, minimizing downtime and disruptions.
Our Governance, Risk, and Compliance (GRC) process is a structured approach that we use to align IT and business strategies with regulatory requirements and manage risks effectively.
- Our Policy Management establishes and maintains policies, procedures, and standards to guide organizational behavior.
- Thereby we ensure Strategic Alignment of business objectives with IT and regulatory requirements.
- Eventually, improved management performance by continuously monitoring and measuring performance against established goals and objectives.
True risk determination in risk assessment within GRC processes involves a systematic approach to identifying, evaluating, and prioritizing risks based on their potential impact and likelihood. Our Experts help you through all the following:
- Risk Identification of Internal and External Sources
- Qualitative Analysis & Quantitative Analysis
- Impact and Likelihood
- Risk Appetite and Tolerance
- Control Measures
- Risk Monitoring and Review
- Continuous Monitoring
Cyber News
Follow our newletter for the latest security feed, threat intelligence and compliances guideline.
Step forward to see your Cyber tools
Our Cyber team always available for your consultation. Whether its a zero day or a ransomeware, We are here to offer your best possible way out. We not only help built Security from ground to up, Also be with you when thing go wrong.
Subscribe to our Newsletter.
Get in touch with our preodic update and services. We do not spam, so you can always unsubscribe. We thank you for choosing protection over lack of enlightment








